Targeted Phishing Scam
A company I consult for was targeted with the a sophisticated email phishing scam.
Analysis
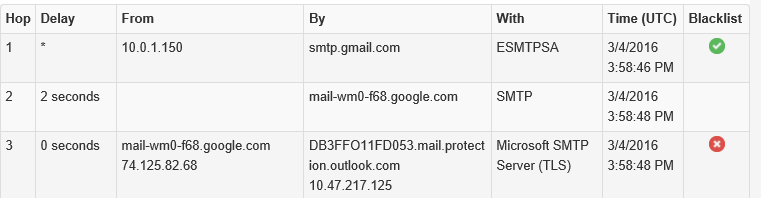
The Hacker did the following;
- Purchased the companyname.technology domain name.
- Acquired the companies email disclaimer.
- Was aware that the company generally add the companies first initial when branding internal systems.
- Sourced approximately 300 seemingly random company email addresses.
- Setup a fake website to steal the employees personal details.
- Registered the domain with a free gmail account.
To make sure the email was delivered to companies employee’s inbox a DomainKeys Identified Mail (DKIM) was created in the companyname.technology public dns. This meant the companies Office 365 Spam Filter Exchange Online Protection could verify the email had not been spoofed ie match the DKIM Stamp that it was expecting and gave the email the lowest possible Spam Confidence level of 1, so the email went to the Inbox instead of junk. 300 is a significant number as this is the threshold for Bulk Email Confidence Level to kick in and potentially flag as Spam.
I recommended the company have register with a service called Gandi, if the companies Trademark is purchased they will be notified. In theory they should be able to report this infringement and block the attack.
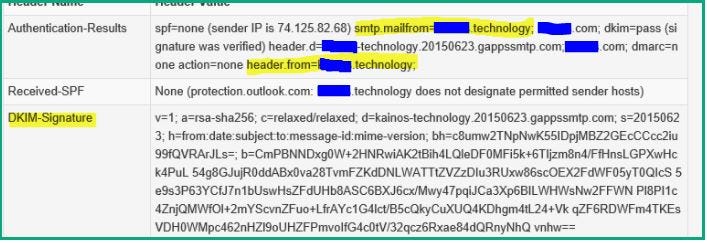
Thankfully this type of hack isn’t the norm. It much easier to spoof an email address eg [email protected] or even [email protected], than purchase the domain. This would mean in the Authenication-Results the email header would be different than highlighted above. They won’t match as the smtp.mailfrom would list the actual spoofed location.
DMARC
DMARC Domain Message Authentication Reporting & Conformance is a global initiative designed to stop email fraud, when the smtp.mailfrom and header.from don’t match, ie if it’s been spoofed. Currently 70% of the worlds inboxes are protected by DMARC.

DMARC protection starts by creating DNS records for Company owned domains. This means that Email Service Providers who have implemented DMARC, notify company of DMARC/Spoofed email failures.
There are 3 different modes to DMARC,
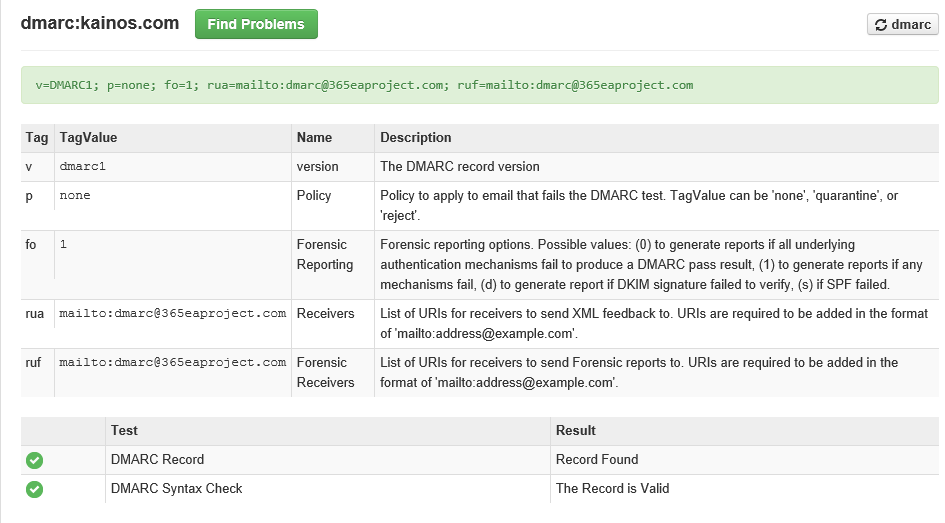
None — does not affect mail flow — forwards the failure to monitoring email address.
Quarantine — does not deliver email — moves the email to quartantine area for inspection
Reject — the goal is to get DMARC in reject mode — failures must be spoofed email and rejected.
Amber Alert — NCA / GDS
The National Crime Agency had issued an Amber warning in January 2016 to businesses who had suffered from Phishing attack to implement DMARC.
Government Digital Services had advised all Government agencies to set the DMARC Record to Reject mode by Oct 2016, this included HMRC https://gdstechnology.blog.gov.uk/2016/06/28/updating-our-security-guidelines-for-digital-services/.
DMARC Alignment
Implementing DMARC is no easy task, the company has several applications that send us email from companyname.com email addresses that aren’t sent from Office 365 for example Salesforce, Workday and mailchimp. Putting DMARC in reject mode straight away would mean important email might be blocked.
I could add Kimble, Workday to our Sender Policy Framework that allows these applications can send email on our domains behalf, but SPF has a limitation of 10 applications. This is were DKIM keys come into play. While DMARC is in “none” — monitoring mode any failures go into a list to have a DKIM added.
Office 365 gave its customers the ability to add DKIM keys in June 2016. This means that when you send an email it is more likely to land in the recipients’ inbox (just like the hacker). Spam filters work on the assumption if you have implemented DKIM you must be trustworthy.
DMARC Failures
Some examples of DMARC failures / spammers pretending to send email from the companyname.com domains below.
3rd Party Help
A company called ReturnPath were one of the companies who started the DMARC initiative, their site is full of useful links that helped implement the DMARC DNS Records, it stated on their website if you needed guidance to give them a call which I did.
I had a very interesting screen share with the Sales Director of Return Path. Email Service Providers share information with certain trusted companies who analyse and produce reports that the ESPs in turn use, for example the Blacklist report is generated by ReturnPath. ISPs and 2 million people share their data with ReturnPath.
6th Top Sender of companyname.com email was spoofed
The Sales Director showed me a list of the top senders of email using the companyname.com domain. The first 5 were Office 365 servers as expected, 7th I assumed was Workday (coming from a Virgin IP), the 6th top sender of emails from companyname.com was a University. The University’s mail server had been compromised and a SpamBot was sending a significant amount of email as the company, NHS Trusts and other brands.
Who can read your email as it transverses the internet?
Another interesting point came up, many organisations (that Microsoft trust) can read your emails unless they are encrypted.
Office 365 Mail Encryption
I implemented encrypted email in Office 365 through transit and at rest. I recommend testing how this work before pushing to customers, but essentially all you needed to do is put [encrypt] in the subject of the email and it will be encrypted.
Conclusion
DMARC can be used to stop criminals from sending email from domain names that you own.
The more companies that implement DMARC the less chance of you getting phished.
DKIM should be implemented to increase the probability of email going to the recipient’s inbox.
Hackers will always have a workaround to exploit, so be vigilant.
Email is visible to Microsoft Trusted 3rd parties as it transverses the internet, if you want to make sure the 3rd parties cannot read your email, encrypt it.